What is Unified threat Management?
Unified threat management (UTM) provides multiple security features and services in a single device or service on the network, protecting users from security threats in a simplified way. UTM includes functions such as anti-virus, anti-spam, content filtering, and web filtering.
How Does UTM Protect Users and Networks?
IT teams are constantly faced with the challenge of protecting their companies’ productivity and digital assets against evolving and sophisticated threats, including spam and phishing attacks, viruses, Trojans and spyware infected files, unapproved website access, and unapproved content. They have to address these challenges with limited budgets and resources. Having multiple separate devices, each designed to perform a specialized function such as spam filtering, web content filtering, or antivirus protection does not make this task easier. Rather, it adds to the cost and complexity of managing multiple boxes and multiple operating systems.
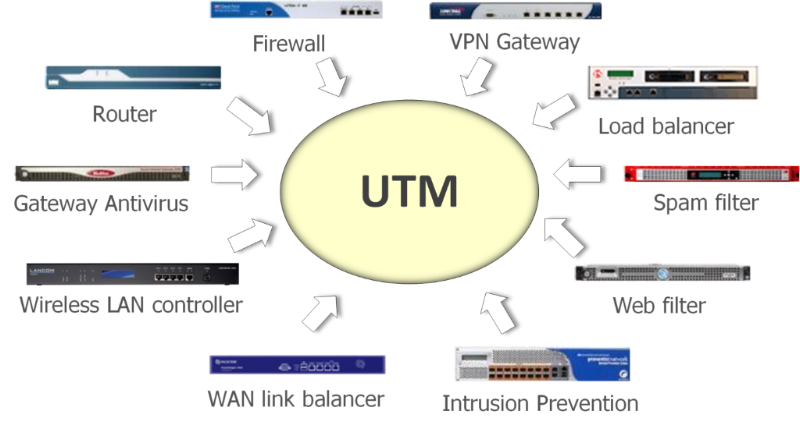
UTM is a single system that provides the answer to all of these challenges and more:
- It secures the network from viruses, malware, or malicious attachments by scanning the incoming data using Deep Packet Inspection.
- It prevents attacks before they enter the network by inspecting the packet headers.
- It prevents access to unwanted websites by installing enhanced web filtering.
- It provides ability to update automatically with the latest security updates, anti-virus definitions, and new features so that minimal manual intervention is required beyond initial set-up.
- It enables administrators to manage a wide range of security functions with a single management console.




















